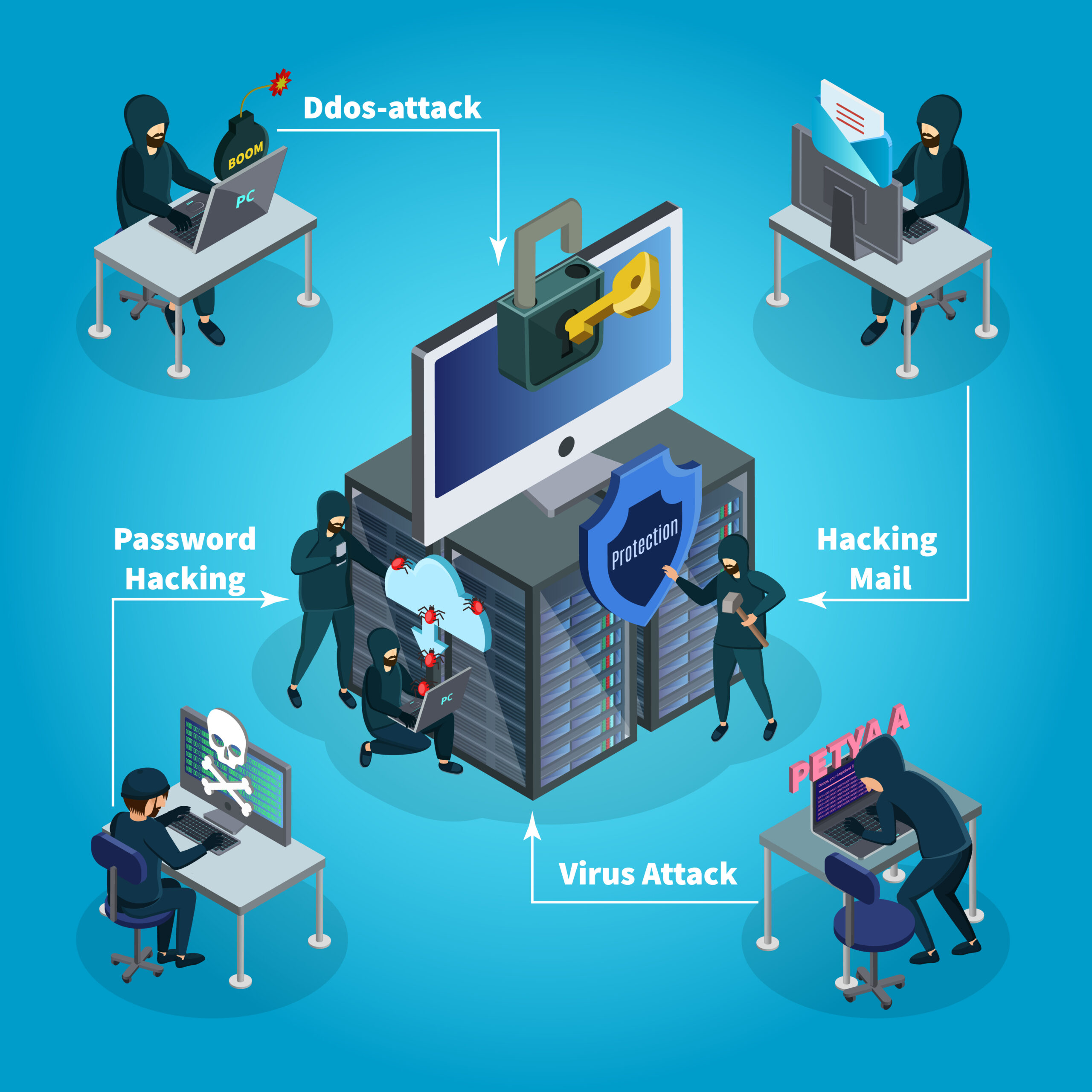
DDoS Attacks: Understanding and Abating Them with Web Hosting
Businesses and individuals alike rely heavily on the internet to transact business, share information, and establish connections in the vast world of cyberspace. However, the constant threat of cyberattacks coexists with the accessibility and convenience that the digital sphere offers. The Distributed Denial of Service (DDoS) attack is one of the most powerful of these attacks. This thorough guide will cover the nuances of DDoS attacks, their possible effects on websites, and practical methods for reducing them with reliable web hosting services.
Deciphering the Enigma of DDoS Attacks
- Explaining DDoS Assaults
The malicious goal of a Distributed Denial of Service (DDoS) attack is to stop legitimate traffic from reaching a specific server, website, or network resource. In contrast to traditional Denial of Service (DoS) attacks, which involve multiple compromised devices working together to form a botnet that the attacker controls, this is known as “zombies” or “bots.” These compromised devices flood the target with traffic, making it unavailable to authorized users. - Operating Modes DDoS attacks can take many different forms, each utilizing a unique set of strategies to overwhelm the target’s resources: Volumetric Attacks: This type overloads the target with a large amount of traffic, using up all of its bandwidth and making it unable to respond to valid requests. Protocol-based Distributed Denial of Service (DDoS) attacks leverage weaknesses or inefficiencies in the underlying infrastructure to overwhelm the target’s resources. Application Layer Attacks: Also referred to as Layer 7 attacks, these attacks focus on the OSI model’s application layer, taking advantage of holes in web servers, applications, or APIs to impede the delivery of services.
The Reasons for The Attacks
DDoS attacks are planned for a variety of reasons, from financial gain to ideological reasons.
- Hacktivism: Hacktivist groups have been known to launch DDoS attacks in protest or retaliation against perceived injustices or ideological rivals.
- Cyberwarfare: nation-states and cybercriminal groups use DDoS attacks as a tactic to compromise operations. Extensively, the infrastructure of other countries or companies.
- Attackers may use DDoS attacks as a means of extorting money from the targeted organizations. They can do this by threatening to stop the attack in exchange for ransom payments.
What DDoS Attacks Affect
- Financial Repercussions
A DDoS attack can have disastrous financial effects on companies of all sizes. The attack caused downtime, which resulted in lost sales, unhappy consumers, and harm to the reputation of the brand. Additionally, companies might have to pay for extra costs related to cleanup operations. Such as building out their cybersecurity infrastructure and hiring forensic specialists to look into the incident. - Damage to Reputation
DDoS attacks have the potential to cause long-term harm to an organization’s reputation in addition to immediate financial losses. Long-term service outages can damage a brand’s reputation. More so, reduce customer loyalty at a time when customer confidence and trust are crucial. Furthermore, the attack’s long-term effects may be exacerbated by adverse media coverage and social media backlash that exacerbate the reputational consequences.
Web hosting solutions for mitigating DDoS attacks
Select a Hosting Provider with DDoS Protection
Give top priority to web hosting companies that include strong DDoS protection measures in their service packages. In order to protect their clients’ uninterrupted service delivery, these providers use advanced network architecture designs. As well as traffic filtering technologies to identify and neutralize it instantly.
Put in place traffic sweeping and rate limitations
Use traffic scrubbing techniques and rate-limiting measures at the network perimeter to lessen the impact of DDoS attacks. By limiting the number of incoming requests from specific IP addresses, rate-limiting controls lessen the effect of volumetric attacks. Before malicious packets can reach the target infrastructure, traffic scrubbing solutions identify and filter them based on their analysis of incoming traffic patterns.
By distributing website content among geographically separated servers, content delivery networks (CDNs) improve scalability and lower latency. CDNs not only enhance website performance but also serve as a defense against DDoS attacks. This is done by dividing incoming traffic among several edge servers, lessening the effect of volumetric attacks, and guaranteeing the best possible user experience.
Implement IPS, or intrusion prevention systems
Intrusion prevention systems (IPS) are real-time network traffic monitoring systems that spot and stop malicious activity before it jeopardizes the integrity of the infrastructure. Organizations can protect vital assets and ensure operational continuity. They can do this by proactively defending against DDoS attacks and other cyber threats by strategically deploying intrusion prevention systems (IPS) at key points within the network architecture.
Perform Frequent Penetration Tests and Security Audits
A thorough cybersecurity plan must include both regular security audits and penetration testing exercises. Organizations can lessen the risk of attacks and other cyber threats by proactively evaluating the resilience of their applications and infrastructure, identifying potential vulnerabilities, and putting remediation measures in place.
Conclusion
To sum up, DDoS attacks pose a serious risk to the confidentiality, integrity, and availability of online resources. Organizations can strengthen their defenses against attacks. They can also protect their digital assets by comprehending the nature of these assaults and putting proactive mitigation strategies into place. Organizations must take a multi-layered approach to cybersecurity. This will help reduce the risk of attacks and guarantee continuous service delivery in an increasingly hostile digital environment. This includes selecting a hosting provider that offers protection against DDoS attacks as well as utilizing advanced traffic filtering and intrusion prevention technologies.