Introduction
Introduction: Are you worried about keeping your online fortress strong and secure? Well, it’s time to introduce you to two important tools – firewalls and intrusion detection systems (IDS). To begin with, firewalls act as the first line of defense, preventing unauthorized access to your network. On the other hand, IDS acts as an early warning system, detecting any unusual behavior on your network. But why do you need both? While firewalls restrict access, IDS ensures any malicious activity doesn’t go unnoticed. Together, they make your online security foolproof. In the era of cyber threats, security has become a crucial aspect for any individual or organization. A single breach can have serious consequences for your data and reputation. Therefore, a comprehensive cybersecurity strategy must include both firewalls and intrusion detection systems to secure your online fortress.
Firewalls: The First Line of Defense
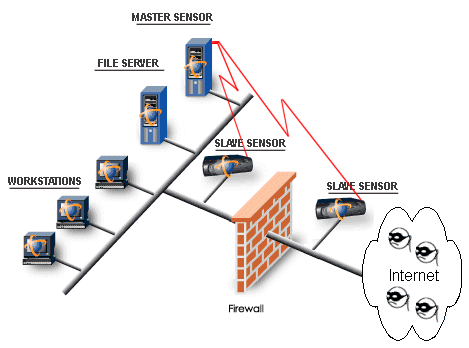
Firewalls: The First Line of Defense When it comes to protecting your online infrastructure, firewalls are the first line of defense. They act as a barrier between your internal network and the external internet, filtering out unwanted traffic and preventing unauthorized access to your systems. But how do firewalls actually work? There are several different types of firewalls, each with their own unique approach to filtering traffic. One common type is a packet-filtering firewall, which examines incoming packets of data and compares them to a set of predefined rules to determine whether they should be allowed through or blocked. Other types of firewalls include application-level gateways, which focus on filtering specific types of traffic such as HTTP or FTP, and stateful inspection firewalls, which maintain a record of ongoing network connections and use that information to make more intelligent filtering decisions. So, how do you choose the right firewall for your business? It depends on your specific needs and the size and complexity of your network. You’ll want to consider factors like cost, ease of use, and the level of control you need over your network traffic. One thing to keep in mind is that firewalls are just one piece of the puzzle when it comes to securing your network. In addition to firewalls, you may also want to consider implementing intrusion detection systems (IDS), which can provide early warnings of potential security threats and help you respond more quickly to attacks. In the next section, we’ll take a closer look at how IDS works and when it makes sense to use it in addition to firewalls.
Intrusion Detection Systems: The Early Warning System
Introduction Detection Systems: The Early Warning System While firewalls act as a barrier to prevent unauthorized access to your network, intruders can sometimes find a way to get through them. This is where Intrusion Detection Systems (IDS) come in, providing an early warning system to detect and alert you to any unauthorized access or suspicious activity on your network. IDS works by monitoring your network traffic and analyzing it for any suspicious patterns or activities. There are two types of IDS: network-based and host-based. Network-based IDS monitors network traffic for any suspicious activity, while host-based IDS monitors your systems and applications for any unusual behavior. When it comes to using IDS in addition to firewalls, the rule of thumb is to use IDS when you need advanced threat detection capabilities beyond what your firewall can do on its own. For example, if your business handles highly sensitive data, such as financial or personal information, you may want to consider using an IDS to provide an additional layer of protection. In addition, IDS can also be useful for detecting insider threats or unauthorized access from within your organization’s network. By monitoring and analyzing network traffic, IDS can detect any unusual behavior that may indicate malicious activity from an internal user. Overall, combining a firewall with an IDS provides a powerful defense against cyber attacks and intrusion attempts. However, it’s important to remember that no cybersecurity solution is foolproof, and ongoing maintenance, monitoring, and updates are crucial to ensure the continued effectiveness of your security measures.
Best Practices for Implementing a Firewall/IDS System
Best Practices for Implementing a Firewall/IDS System: Understanding your network architecture is the cornerstone of setting up an effective firewall/IDS system. This includes identifying critical business assets, locating potential vulnerabilities, and mapping out your network traffic flow. Once you have a solid understanding of your network architecture, configuring your firewall/IDS becomes much easier. Pay attention to the types of traffic being sent through each port and configure your firewall/IDS accordingly. Be sure to set up precise rules to avoid any unnecessary traffic. Setting up alerts and notifications is another key aspect of an effective firewall/IDS system. Configure your system to send alerts to the right people at the right time. Remember, alerts can only be helpful if someone is there to address them. Finally, ongoing maintenance and review are critical to keeping your firewall/IDS system functioning properly. Regularly test your system and keep your software up to date. Remember, an out-of-date system is an invitation to hackers. By taking these best practices into consideration, you can set up an effective firewall/IDS system that will help keep your online fortress secure.
Common Mistakes to Avoid
Common Mistakes to Avoid: Assuming a Firewall is Enough: Firewalls are a necessary component of any cybersecurity strategy. They filter the incoming traffic to your network, keeping out unwanted visitors. However, relying solely on a firewall is a major mistake. Firewalls can only protect your network from known threats, not new and emerging ones. Hackers are constantly developing new ways to infiltrate systems, and firewalls alone are not enough to stop them. Neglecting Regular Updates and Maintenance: Your firewall and intrusion detection system are only as effective as their latest updates. Neglecting regular maintenance and updates is a major mistake that can leave your system vulnerable to attack. Failing to keep your system updated can lead to new vulnerabilities that hackers can exploit. Your firewall and IDS must be regularly updated and maintained to stay effective against new threats. Relying Too Much on Automated Alerts: Automated alerts are a useful tool for monitoring your network, but they are not foolproof. Relying too much on automated alerts can lead to complacency and missed threats. It’s essential to have a security professional in place who can interpret the alerts and take appropriate action. Automated alerts should be treated as a supplement to manual monitoring, not a replacement. Ignoring Alerts and Warnings: One of the biggest mistakes you can make in cybersecurity is ignoring alerts and warnings. Too often, employees are distracted or overwhelmed and fail to respond to security alerts. This can be disastrous for your network, leaving it vulnerable to attack. It’s essential to have a plan in place for responding to alerts and educating employees on the importance of taking them seriously. In short, relying solely on a firewall, neglecting regular maintenance, relying too much on automated alerts, and ignoring warnings are major mistakes to avoid. Keep your cybersecurity strategy up to date and ensure that you have a team in place to monitor and respond to threats.
Conclusion
Recap of Key Points: Firewalls and intrusion detection systems are critical components of a comprehensive cybersecurity strategy. Firewalls act as the first line of defense, while intrusion detection systems provide early warning of potential attacks. Choosing the right firewall and IDS for your business, as well as ongoing maintenance and review, are essential best practices. However, it’s important to avoid common mistakes like relying too heavily on automated alerts and neglecting regular updates. By implementing a strong firewall and IDS system and remaining vigilant, you can strengthen your online fortress and protect your business from cyber threats.